Nos roteadores Cisco podemos gerar certificados auto-assinados, mas também podemos instalar certificados de outras entidades certificadoras, o que faz até mais sentido para ambientes em produção.
O roteador pode usar o certificado para autenticar uma VPN site to site, por exemplo.
Considerando que o roteador já tenha a configuração básica (hostname e domain-name), esse são os passos para gerar um CSR, instalar o certificado root (entidade certificadora) e também o certificado do roteador (assinado pela CA).
1) Gerando o CSR e o Certificado do roteador
O primeiro passo é gerar uma solicitação de certificado. Para isso vamos criar um trustpoint e fornecer as informações que constarão no certificado.
Existem formas para que a solicitação seja feita diretamente entre roteador e a CA, mas neste exemplo será feita manualmente.
BrainRT01#conf t BrainRT01(config)#crypto pki trustpoint MSCALAB BrainRT01(ca-trustpoint)#fqdn brainrt01.brainwork.local BrainRT01(ca-trustpoint)#subject-name CN=brainrt01.brainwork.local,O=Lab, C=BR BrainRT01(ca-trustpoint)#enrollment terminal BrainRT01(ca-trustpoint)#exit BrainRT01(config)#crypto pki enroll MSCALAB % Start certificate enrollment .. % The subject name in the certificate will include: CN=brainrt01.brainwork.local,O=Lab, C=BR % The subject name in the certificate will include: brainrt01.brainwork.local % Include the router serial number in the subject name? [yes/no]: no % Include an IP address in the subject name? [no]: no Display Certificate Request to terminal? [yes/no]: yes Certificate Request follows: MIIC0TCCAbkCAQAwazELMAkGA1UEBhMCQlIxEjAQBgNVBAoTCUxhYiBBZGRlZDEg MB4GA1UEAxMXc3Bva2UyLmxhYi5hZGRlZC5jb20uYnIxJjAkBgkqhkiG9w0BCQIW F3Nwb2tlMi5sYWIuYWRkZWQuY29tLmJyMIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8A MIIBCgKCAQEArueBays0GcaDwX8lg5q6WyGIVhlSk0zXhLopxnnaWmRq0Z2+tkmY bV0O/NqprVEzcGX5ttFGCS74vB2kJVFtrDdZXGDFS6MwlbMzxacy2Ind5CMQXjg7 EhrwZc5M+ZCRQLRtW9ZshXAcuKCJvVAmfnimoA6gA1nPccSTMM6C/3cSnICmh6NG tlgyYylm9emNLLFWRc3tD2ORw2BDfKuGVlLWoXP2rQmyjXfyrr/WPPbicxz4WB7H bSIYv19FG3qTb05d+60jbnz7dc59WKl7q/8XJ/DjH9tbOgWW6X5sRSWGVbN0tKja lRiFnu6BLH5NXJ8ASr7WGdFB7LhouMPKxwIDAQABoCEwHwYJKoZIhvcNAQkOMRIw EDAOBgNVHQ8BAf8EBAMCBaAwDQYJKoZIhvcNAQEFBQADggEBAHYO1bhEmIxK4fu+ UNldaGU4YKIYIF5MiBpTFhdHQ/zTueSrtHl56b+o1PA4HSsWX25ssiZ6Nbt+D55H cjk2o/Z95xZmaV3//TyJnDLqgN+trYXJpAWculk0a+LEoBwlbKkaKyhteT0gS45+ +LC0wslYISjp1cx3t+RR1RFxAC1lYdZ4+kvlxTqKfPw8Sb02RZSRza+ryOBaNi2Y 9RrqyRvkeS4lYqqUBYUMbk4A27hdZUKz0RLDJYMiJ49AZS/KOPHXnFB4RGjLIN4Y 0YjPkKt9jLUR/RvgtaEdihWVGx6DsjdneIehYWks061UHSWKlbUnRcOVBDus5CGg B4ig52s= ---End - This line not part of the certificate request--- Redisplay enrollment request? [yes/no]: no BrainRT01(config)#
Copie a informação do terminal, e no caso de um entidade certificadora Microsoft, abra o browser e selecione a opção Request a certificate > Advanced certificate request > Submit a certificate request by using a base-64-encoded… Cole seu CSR. Selecione o template utilizado para VPN (o nome do template pode variar, mas geralmente é IPSEC).
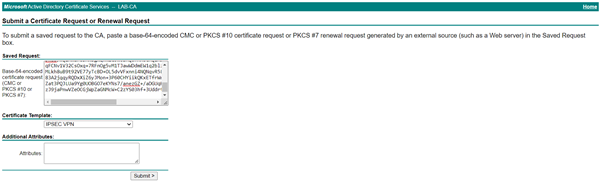
Clique submit, selecione a opção Base 64 encoded e baixe o certificado do roteador que foi assinado pela CA.

2) Certificado Root
Volte para a página home da CA e selecione a opção Base 64 e clique em Download CA Certificate. Salve e abra o arquivo.
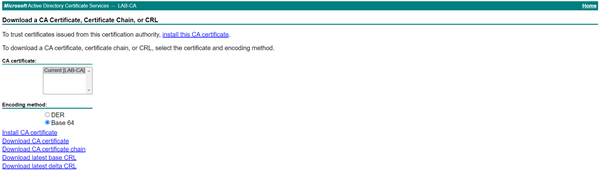
No roteador, digite o comando crypto pki authenticate NOME DO TRUSTPOINT e cole as informações.
BrainRT01(config)#crypto pki authenticate MSCALAB Enter the base 64 encoded CA certificate. End with a blank line or the word "quit" on a line by itself -----BEGIN CERTIFICATE----- MIIDwTCCAqmgAwIBAgIQR2CJiqOG84RJl3BTFdf1FzANBgkqhkiG9w0BAQsFADBm MRIwEAYKCZImiZPyLGQBGRYCYnIxEzARBgoJkiaJk/IsZAEZFgNjb20xFTATBgoJ kiaJk/IsZAEZFgVhZGRlZDETMBEGCgmSJomT8ixkARkWA2xhYjEPMA0GA1UEAxMG TEFCLUNBMCAXDTIxMDUyNjE3MzkyOVoYDzIwNTEwNTI2MTc0OTI3WjBmMRIwEAYK CZImiZPyLGQBGRYCYnIxEzARBgoJkiaJk/IsZAEZFgNjb20xFTATBgoJkiaJk/Is ZAEZFgVhZGRlZDETMBEGCgmSJomT8ixkARkWA2xhYjEPMA0GA1UEAxMGTEFCLUNB MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAu7AC7N0skKdyHJemjUPH xKHTofO1a6p9ZYs5BEe+d3Ye/pgtN6ifSOpjfBHSnk20GqriEoUuA8L0VmDxkzXT Iq2heNhyJVxtJTJglxfuXhapaoAGlU80U6iQ5+6Z/iCIdTDVWxRtfxbSqzjis4fz ZZKTiz3TlU4b9OtbvtimRfu+1Yt1qOFxsjs96vBbu9mq9xnZttOdMon6x3YZ2SMj xovhOERe18HOKdcVjJLpvvdLxcO2BoZVmxxqPEadXtGdMBvzfILfsDcSHtTBLAfN OtW0rv/dfuE5G1CXi2QYzvEBSIWuLMODGiWA9Fl/EzsT9DYwWL/d3he4NLe1QRoj VQIDAQABo2kwZzATBgkrBgEEAYI3FAIEBh4EAEMAQTAOBgNVHQ8BAf8EBAMCAYYw DwYDVR0TAQH/BAUwAwEB/zAdBgNvHQ4EFgQUiNUGEcpPFok8r4Z1ovlblZTwWREw EAYJKwYBBAGCNxUBBAMCAQAwDQYJKoZIhvcNAQELBQADggEBAF2WX/XQsMNqcYcm d62mVZyo//oDy5huJpyausc3LteCMIVNLxy5vCktBPslScNSVF2zOijanJ5rXqXE TVaxYnda/TBa7tOAuOAo5t1JsxyqXPXn80t0llqCg8ol9AZpBZ7XRDgIr2ggTgTT lTE9LrwljEa49AlTOjQXtkxia3rlIf9gBNA2yt7N95nt5mTvsTryCGrOkHgj4eiZ iY65r8IxSDDiFwQBd8ofDcJQxlvpQsfXRNpEnG/z5cMoKo9Z2ftbs1EyVb/rLBok kra2Zynd8gvHMex1aqvOgMEMRT1evkJRwf6wX+loSc08kAm5GNXuJK10TzW+UjA8 npXodBA= -----END CERTIFICATE----- quit Certificate has the following attributes: Fingerprint MD5: 8425DC19 D2E2CB36 AA4A5F7A 1B9D6A5F Fingerprint SHA1: 41BAD21A B4764442 72BE4D5F A573B48B 57E9734F % Do you accept this certificate? [yes/no]: yes Trustpoint CA certificate accepted. % Certificate successfully imported BrainRT01(config)#
Se você tiver uma entidade intermediária também é necessário instalar o certificado dela no roteador.
3) Importando o Certificado do roteador
Agora com o certificado da CA já autenticado no roteador, vamos instalar o certificado do próprio roteador, que foi assinado pela CA (arquivo gerado no passo 1).
BrainRT01(config)#crypto pki import MSCALAB certificate Enter the base 64 encoded certificate. End with a blank line or the word "quit" on a line by itself -----BEGIN CERTIFICATE----- MIIFqzCCBJOgAwIBAgITEQAAAB4Z7IPQ9lMo1wAAAAAAHjANBgkqhkiG9w0BAQsF ADBmMRIwEAYKCZImiZPyLGQBGRYCYnIxEzARBgoJkiaJk/IsZAEZFgNjb20xFTAT BgoJkiaJk/IsZAEZFgVhZGRlZDETMBEGCgmSJomT8ixkARkWA2xhYjEPMA0GA1UE AxMGTEFCLUNBMB4XDTIyMDYyMzIxMzUzOVoXDTI0MDYyMjIxMzUzOVowQzELMAkG A1UEBhMCQlIxEjAQBgNVBAoTCUxhYiBBZGRlZDEgMB4GA1UEAxMXc3Bva2UyLmxh Yi5hZGRlZC5jb20uYnIwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQCu 54FrKzQZxoPBfyWDmrpbIYhWGVKTTNeEuinGedpaZGrRnb62SZhtXQ782qmtUTNw Zfm20UYJLvi8HaQlUW2sN1lcYMVLozCVszPFpzLYid3kIxBeODsSGvBlzkz5kJFA tG1b1myFcBy4oIm9UCZ+eKagDqADWc9xxJMwzoL/dxKcgKaHo0a2WDJjKWb16Y0s sVZFze0PY5HDYEN8q4ZWUtahc/atCbKNd/Kuv9Y89uJzHPhYHsdtIhi/X0UbepNv Tl37rSNufPt1zn1YqXyr/xcc8OMf21s6BZbpfmxFJYZVs3S0qNqVGIWe7oEsfk1c nwBKvtYZ0UHsuGi4w8rHagMBAAGjggJzMIICbzAOBgNVHQ8BAf8EBAMCBaAwHQYD VR0OBBYEFN4A8BfS64MlVX0fSBe1Lwb6ZrSYMB8GA1UdIwQYMBaAFIjVBhHKTxaJ PK+Ge6L5W5WU8FkRMIHPBgNVHR8EgccwgcQwgcGggb6ggbuGgbhsZGFwOi8vL0NO PUxBQi1DQSxDTj1sYWJkYzAxLENOPUNEUCxDTj1QdWJsaWMlMjBLZXklMjBTZXJ2 aWNlcyxDTj1TZXJ2aWNlcyxDTj1Db24maWd1cmF0aW9uLERDPWxhYixEQz1hZGRl ZCxEQz1jb20sREM9YnI/Y2VydGlmaWNhdGVSzXZvY2F0aW9uTGlzdD9iYXNlP29i amVjdENsYXNzPWNSTERpc3RyaWJ2dGlvblBvaW50MIHDBggrBgEFBQcBAQSBtjCB szCBsAYIKwYBBQUHMAKGgaNsZGFwOi8vL0NOPUxBQi1DQSxDTj1BSUEsQ049UHVi bGljJTIwS2V5JTIwU2VydmljZXMsQ049U2VydmljZXMsQ049Q29uZmlndXJhdGlv bixEQz1sYWIsREM9YWRkZWQsREM9Y29tLERDPWJyP2NBQ2VydGlmaWNhdGU/YmFz ZT9vYmplY3RDbGFzcz1jZXJ0aWZpY2F0aW9uQXV0aG9yaXR5MD0GCSsGAQQBgjcV BwQwMC4GJisGAQQBgjcVCIKy/GuD56oqyZklhNKMboaNxSuBXYbhhkuGzJxZAgFk AgEEMB0GA1UdJQQWMBQGCCsGAQUFBwMBBggrBgEFBQgCAjAnBgkrBgEEAYI3FQoE GjAYMAoGCCsGAQUFBwMBMAoGCCsGAQUFCAICMA0GCSqGSIb3DQEBCwUAA4IBAQAE hBDQFVt8L7IQwqmbbFeECqKJLElZ7Y9C4ijHuWWNQAGCmuQgryOtLAAbI5yEonVX UpnkEszrpUmxJbZxDaH0BINHJ7mVzufpo48txgouUcYryqgIJFWITEy4HPK3Vh+m r0G7kYNaf4LTXbyuthsga8s+dxSAEg8CszbposSUHKSktgCgbCbbt2EtIIuQ8HUC eDUBhkNa8ScpYaguF0g+M/oScc8dpN7jOkzOKwDA2tQ54ErHhQ0tWEJ82VbD4cjA +bS/zM86ccxohCLPpXzIC3hq5Jf3/E+t6yeK+E/dDDroFZaZ5xxlUJi8jZbM7M8k lBREGsbooupHcwi3vcg8 -----END CERTIFICATE----- quit % Router Certificate successfully imported BrainRT01(config)#
Pronto! Para validar, basta usar o comando show crypto pki certificates, que listará os certificados instalados no roteador.
BrainRT01#show crypto pki certificates Certificate Status: Available Certificate Serial Number (hex): 110000001E19EC83D0F65328D700000000101G Certificate Usage: General Purpose Issuer: cn=LAB-CA dc=brainwork dc=local Subject: Name: brainrt01.brainwork.local cn=brainrt01.brainwork.local o=Lab c=BR CRL Distribution Points: ldap:///CN=LAB-CA,CN=labdc01,CN=CDP,CN=Public%20Ke,CN=Services,CN=Config,DC=lab,DC=brainwork,DC=local?certificateRevList?base?objec=cRLDistt Validity Date: start date: 18:35:39 GMT Jun 23 2022 end date: 18:35:39 GMT Jun 22 2024 Associated Trustpoints: MSCALAB CA Certificate Status: Available Certificate Serial Number (hex): 4760898AA386F3844997705315D7F517 Certificate Usage: Signature Issuer: cn=LAB-CA dc=brainwork dc=local Subject: cn=LAB-CA dc=brainwork dc=local Validity Date: start date: 14:39:29 GMT May 26 2021 end date: 14:49:27 GMT May 26 2051 Associated Trustpoints: MSCALAB
Note que o certificado está disponível no roteador, mas para usá-lo outras configurações são necessárias, de acordo com a necessidade.
Neste link temos o exemplo de como usar o certificado para uma VPN site to site. No exemplo é um ASA, mas serve de roteiro.
Até a próxima.



You must be logged in to post a comment.